How to crack Wi-Fi?
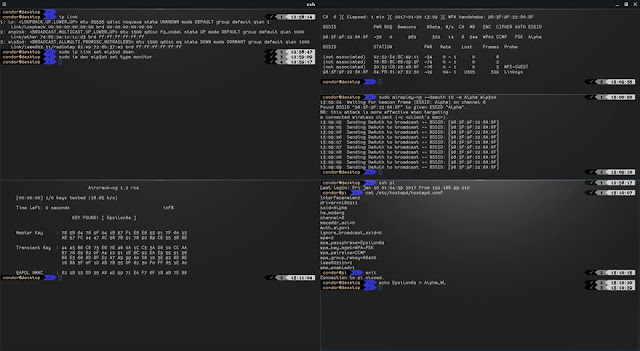
How to crack Wi-Fi? I'll explain it to you in a few simple steps. Assumed is that you know how to boot up a Linux environment and how to install a package in it. Ok so first things first. In your Linux distribution install the package "aircrack-ng". It's a suite with some very useful Wi-Fi cracking tools. We'll use 3 of them here. Identify your Wi-Fi card and put it into monitor, as shown in the top left terminal. Mine is wlp3s0. Next, start capturing all traffic from a specific access point. In the top right terminal I've used the following command: $ sudo airodump-ng --essid Alpha -c 6 --write Alpha_CAP wlp3s0 Which means: - Capture the AP that identifies as Alpha. - Stay on channel 6 during the capturing. - Write the output files using Alpha_CAP filename. Then we need to get some users to authenticate to the AP and capture the handshake, as shown in the middle right terminal. You can see that you captured the key when the airodump-ng termin...



